Cryptic codes and ciphers have amazed people for centuries. From ancient times to modern day encryption, these methods have kept secrets safe and puzzled even the smartest minds. Let’s explore some of the most famous codes and ciphers that have enthralled us over the years.
This post will dive into both solved and unsolved mysteries of the cryptographic world. We’ll look at their history, how they work, and why they still matter today.
15 Cryptic codes and Ciphers (Short Details):
- The Caesar Cipher: A simple yet effective ancient cipher used by Julius Caesar to secure military messages.
- The Enigma Machine: A complex encryption device used by Nazi Germany during World War II, cracked by Allied codebreakers.
- The Vigenère Cipher: An advanced cipher using a keyword for multiple shifts, once thought unbreakable.
- The Zodiac Killer Ciphers: Mysterious ciphers sent by the infamous Zodiac Killer, with some remaining unsolved.
- The Voynich Manuscript: An undeciphered manuscript filled with strange symbols and mysterious illustrations.
- The RSA Algorithm: A cornerstone of modern encryption securing online communications and data.
- The Playfair Cipher: A digraph substitution cipher used for secure communication in the 19th century.
- The Pigpen Cipher: A simple geometric substitution cipher popular among secret societies like the Freemasons.
- The Beale Ciphers: Three cryptic documents hinting at a hidden treasure, with two still unsolved.
- The Great Cipher of Louis XIV: A powerful French cipher that protected secrets for 200 years.
- The Dancing Men Cipher: A fictional cipher from Sherlock Holmes, inspiring real cryptographic interest.
- The Navajo Code Talkers: Native American code creators who helped the Allies in World War II with an unbreakable code.
- The Book Cipher: A cipher using common books as keys for secure communication during wars.
- The Chaocipher: An unbreakable cipher invented in the 1920s, challenging cryptographers even today.
- The RSA 2048-Bit Key Challenge: A modern challenge to crack a powerful encryption method protecting online data.
1. The Caesar Cipher

The Caesar Cipher is one of the oldest known codes. It was used by Julius Caesar to send secret messages to his generals. The method shifts letters in the alphabet by a fixed number.
While it might seem simple today, it was highly effective in its time. The key to decoding is knowing the number of shifts. Even now, it’s a popular example in beginner cryptography lessons.
Its simplicity makes it easy to understand but also shows the basics of encryption. Many modern techniques are built on these early ideas.
Read more: Caesar Cipher in Cryptography
2. The Enigma Machine

The Enigma Machine was a complex cipher device used by Nazi Germany during World War II. It scrambled messages in a way that seemed impossible to decode. Each letter was substituted by another, making it extremely difficult to crack.
Allied codebreakers, including Alan Turing, worked tirelessly to break the Enigma code. Their success played a huge role in the outcome of the war. The machine’s code-breaking marked the beginning of computer science and modern cryptography.
Even today, the story of the Enigma Machine is a symbol of how codes and ciphers can change the course of history.
3. The Vigenère Cipher

The Vigenère Cipher is a step up from simple substitution ciphers. It uses a keyword to create multiple shifts, making it much harder to crack. For centuries, it was considered unbreakable.
It wasn’t until the 19th century that a mathematician finally solved it. The Vigenère Cipher taught cryptographers that even complex codes could be broken with the right technique.
Today, it serves as an example of how cryptography has evolved. It shows the constant battle between code makers and code breakers.
4. The Zodiac Killer Ciphers

The Zodiac Killer sent mysterious ciphers to newspapers in the 1960s. Some of these codes were cracked, but others remain unsolved. The ciphers included letters, symbols, and numbers, leaving many to wonder what they mean.
Despite countless attempts, a few of these codes still puzzle experts. They are a mix of known techniques and creative twists that make them unique.
The Zodiac ciphers have kept both amateur and professional cryptographers busy for decades. The mystery behind them fuels ongoing fascination.
Read More: 15 Popular Conspiracy Theories: Fact vs. Fiction
5. The Voynich Manuscript

The Voynich Manuscript is a handwritten book filled with strange symbols and illustrations. Discovered in the 15th century, it remains undeciphered to this day. Some believe it’s a code, while others think it’s a language we don’t understand.
Scientists, historians, and cryptographers have all tried to crack it, but none have succeeded. Its origins and purpose remain a mystery.
Whether it’s a code or a hoax, the Voynich Manuscript continues to capture fancies worldwide.
Read more: An Intoxicating 500-Year-Old Mystery
6. The RSA Algorithm

The RSA Algorithm is a cornerstone of modern encryption. It’s used to secure online communications, banking, and data. It relies on two large prime numbers to create a code that’s hard to break.
This method is effective because it takes immense computing power to crack it. Even with today’s technology, it remains one of the most secure cryptographic techniques.
Understanding RSA helps us see how math protects our digital world. It’s a reminder of how far cryptography has come since its ancient roots.
7. The Playfair Cipher
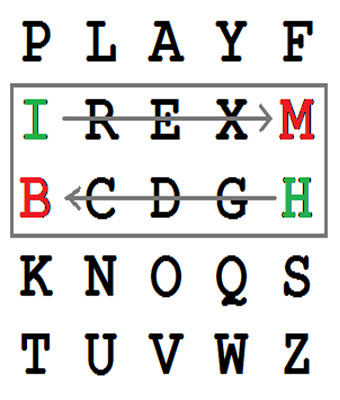
The Playfair Cipher was popular in the 19th century. It was used in World War I for secure communication. Instead of shifting letters, it encrypts pairs of letters, making it harder to decode.
It was one of the first practical digraph substitution ciphers. Breaking it required knowledge of letter frequencies and patterns. Even today, it remains a favourite among puzzle enthusiasts.
Its historical use in espionage shows the importance of ciphers in wartime. It also highlights how codes can adapt to new needs and situations.
Read More: 15 Unsolved Disappearances That Will Haunt You
8. The Pigpen Cipher
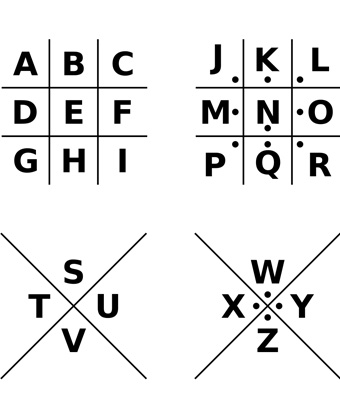
The Pigpen Cipher looks like a child’s game, but it has a long history. It uses geometric symbols instead of letters, making it visually unique. Secret societies like the Freemasons often used it.
The symbols are easy to learn, making it accessible for beginners. Many people still use it for fun or to send secret messages.
Though it’s simple, the Pigpen Cipher shows how varied and creative codes can be. It’s proof that even basic ciphers have their place in history.
9. The Beale Ciphers

The Beale Ciphers are three mysterious documents that supposedly reveal the location of hidden treasure. Only one has been decoded, and it describes how to crack the other two.
Treasure hunters and cryptographers have been trying to solve the remaining ciphers for over a century. Some believe they’re genuine, while others think they’re a hoax.
Regardless of the truth, the Beale Ciphers remain one of the most talked-about cryptographic mysteries. The thrill of the unknown keeps people interested.
Read more: The Beale Ciphers: Virginia’s Modern-Day DaVinci Code
10. The Great Cipher of Louis XIV
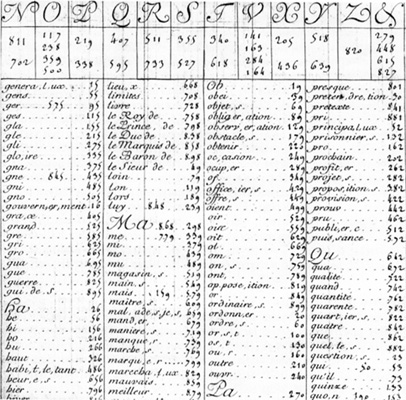
The Great Cipher was created by the Rossignols, a father-son duo who served Louis XIV. It was so secure that it protected French secrets for 200 years. It used a complex system of numbers to substitute syllables.
It wasn’t until the 1890s that it was finally cracked. This breakthrough revealed many hidden messages from the French court.
The Great Cipher shows how long a well-made code can last. It stands as a challenge to cryptographers even today.
11. The Dancing Men Cipher
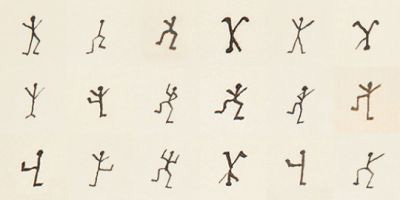
The Dancing Men Cipher comes from a Sherlock Holmes story. It uses stick figures in different poses to represent letters. The code was fictional but flickered real interest.
Fans of puzzles often use it in games and challenges. It shows how stories and pop culture can inspire real cryptographic methods.
Even though it’s not a real cipher, the Dancing Men Cipher has become a fun way to learn about codes. It shows that cryptography isn’t just for experts.
12. The Navajo Code Talkers
During World War II, the U.S. military used Navajo speakers to create a unique code. The Navajo language was unwritten and complex, making it perfect for secure communication. The code was never broken by the Axis powers.
The Navajo Code Talkers played a crucial role in many battles. Their efforts saved countless lives and helped end the war.
Their story is a reminder of how language itself can be a powerful tool in cryptography.
13. The Book Cipher

A Book Cipher uses a common book to encode messages. Each word or letter is referenced by its position in the text. It’s simple yet effective when the book is only known to the sender and receiver.
Famous cases, like spies using it during wars, show its real-world application. It’s easy to create but hard to break without the key.
The Book Cipher remains popular because it requires no special equipment. It proves that simplicity can often be powerful.
14. The Chaocipher
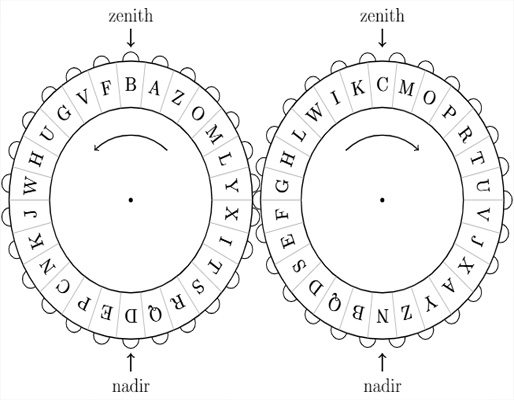
The Chaocipher was invented by John F. Byrne in the 1920s. He claimed it was unbreakable and kept the method secret for decades. Only after his death was it revealed to the public.
It uses a unique mechanical process that combines shifting and substitution. Even today, it’s a challenge for cryptographers to solve.
The Chaocipher reminds us that new ideas in cryptography can come from anywhere. It also shows that secrecy itself can be part of a cipher’s mystique.
15. The RSA 2048-Bit Key Challenge
The RSA 2048-Bit Key Challenge is a modern test of cryptographic strength. It’s a call to crack a code that protects most online communications. Despite many attempts, the challenge remains unsolved.
The difficulty lies in the math behind RSA encryption. It would take thousands of years for current computers to break it.
This challenge shows how far cryptography has come and how it continues to protect our digital lives.
Read more: How a quantum computer could break 2048-bit RSA encryption in 8 hours
Final note:
Codes and ciphers are more than just puzzles; they’re part of our history and our future. They protect secrets, solve mysteries, and even save lives.
As we move into a more digital world, understanding these cryptic methods becomes even more important. Keep exploring, and you might find a code that needs cracking.
15 FAQs (Frequently Asked Questions):
-
What is the Caesar Cipher, and how does it work?
The Caesar Cipher is an ancient method where letters are shifted by a fixed number, making it a simple substitution cipher.
-
How did the Enigma Machine impact World War II?
The Enigma Machine encrypted German messages, and breaking it helped the Allies gain a strategic advantage in the war.
-
Why was the Vigenère Cipher considered unbreakable for centuries?
The Vigenère Cipher uses a repeating keyword to shift letters, making patterns harder to detect compared to simpler ciphers.
-
What makes the Zodiac Killer ciphers so mysterious?
The Zodiac Killer ciphers include unsolved codes with symbols, letters, and numbers, keeping experts puzzled for decades.
-
Why is the Voynich Manuscript still undeciphered?
The Voynich Manuscript’s strange symbols and unknown language have resisted all attempts at decoding, leaving its meaning unknown.
-
How does the RSA Algorithm keep online data secure?
The RSA Algorithm uses two large prime numbers to encrypt data, which is extremely difficult to crack without the decryption key.
-
What makes the Playfair Cipher different from other ciphers?
The Playfair Cipher encrypts pairs of letters, making it more complex than simple substitution ciphers.
-
How is the Pigpen Cipher used today?
The Pigpen Cipher is often used for fun, in puzzles, or by those interested in secret codes and ciphers.
-
What is the story behind the Beale Ciphers?
The Beale Ciphers are three documents said to lead to hidden treasure; only one has been decoded, leaving two unsolved.
-
How was the Great Cipher of Louis XIV cracked after 200 years?
The Great Cipher was finally cracked in the 1890s by a French cryptographer using innovative decryption techniques.
-
Why is the Dancing Men Cipher significant in cryptography?
Though fictional, the Dancing Men Cipher from Sherlock Holmes sparked real interest in cryptographic methods.
-
Who were the Navajo Code Talkers, and what did they do?
The Navajo Code Talkers were Native Americans who developed an unbreakable code used by the U.S. military during World War II.
-
How does a Book Cipher work?
A Book Cipher uses the position of words or letters in a common book as a key for encoding messages.
-
What makes the Chaocipher unique among other ciphers?
The Chaocipher combines shifting and substitution in a mechanical process, making it difficult to crack.
-
What is the RSA 2048-Bit Key Challenge, and why is it important?
The RSA 2048-Bit Key Challenge is a modern test of encryption strength, protecting most online communications today.




